Section 3: The ATTACK Model
Section 3: The ATT&CK ModelSection 3.1: The ATT&CK Matrix
Section 3.2: Technology Domains
Section 3.3: Tactics
Section 3.4: Techniques and Sub-Techniques
Section 3.5: Groups
Section 3: The ATT&CK Model
ATT&CK is a knowledge base of adversarial techniques. However, unlike prior work in this area, the focus isn't on the tools and malware that adversaries use but on how they interact with systems during an operation.
Section 3.1: The ATT&CK Matrix
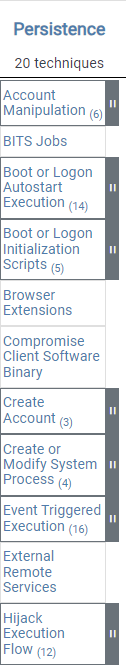
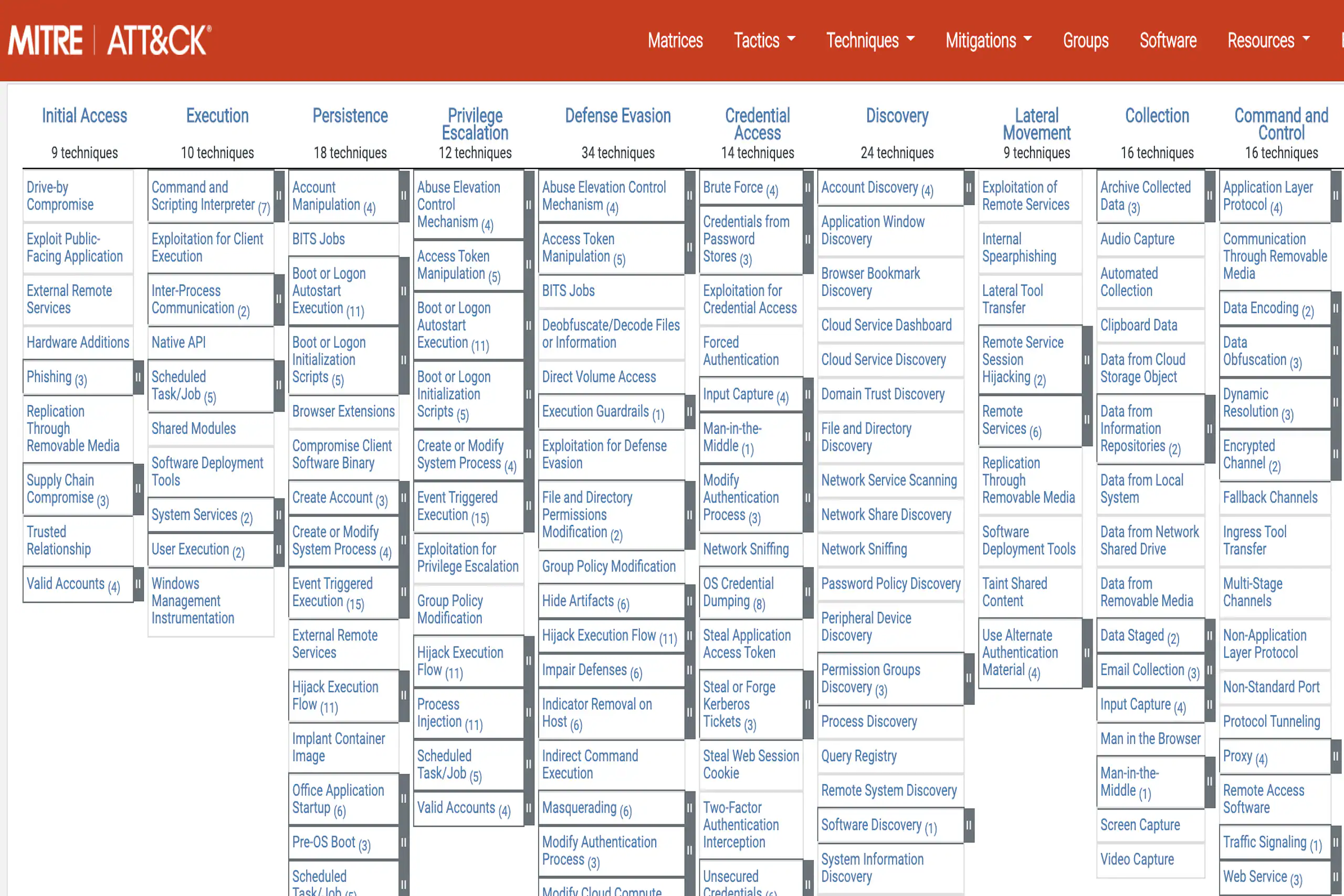
The ATT&CK Matrix is a visual representation of the relationship between tactics and techniques.
 MITRE ATT&CK Matrix Website
MITRE ATT&CK Matrix WebsiteThe Persistence column, shows that there are 20 techniques that an attacker may use to attempt to gain persistence in an environment.
Some techniques break down into sub-techniques; when reviewing the first technique, Account Manipulation, you'll find six listed sub-techniques.
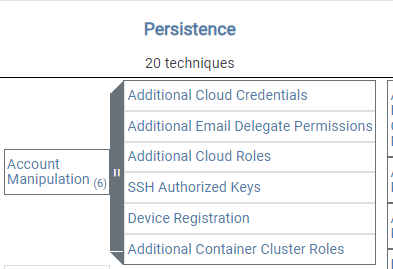
To learn more about each sub-techniques click here here
Section 3.2: Technology Domains
Platform - the system an adversary is operating within.
MITRE has defined three technology domains and these domains have platforms attached to them:
- Enterprise (traditional enterprise networks and cloud technologies) - Linux, macOS, Windows, AWS, Azure, GCP, SaaS, Office 365, Azure AD
- Mobile - Android, iOS
- Industrial Control Systems (ICS)
Section 3.3: Tactics
Tactics answers the "why" question of an attack technique, explaining the adversary's objective for performing an action.
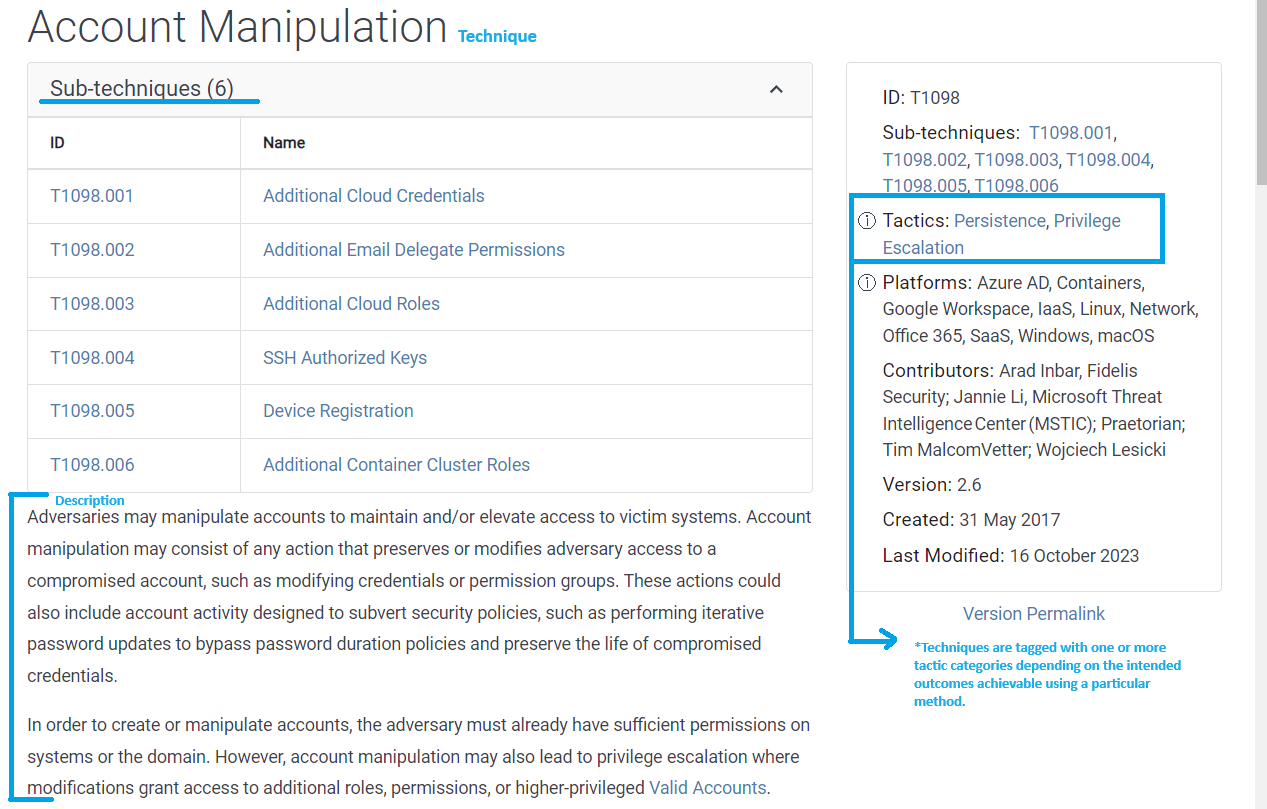
Each technique (for example, the persistence column above) or sub-technique, (for example, account manipulation) is associated or tagged with one or more tactic categories depending on the intended outcomes achievable using a particular method. A definition is provided for each Tactic, describing the category it falls under; this definition works as a guide for what techniques should be under the Tactic.
Section 3.4: Techniques and Sub-Techniques
Using the Additional Cloud Credentials example, an adversary can create new cloud service accounts or add new credentials to existing accounts to keep access to cloud resources even if the original access credentials are revoked.
Section 3.4.1: Procedures
Procedures refer to adversaries' step-by-step actions using specific techniques or sub-techniques to achieve their goals.
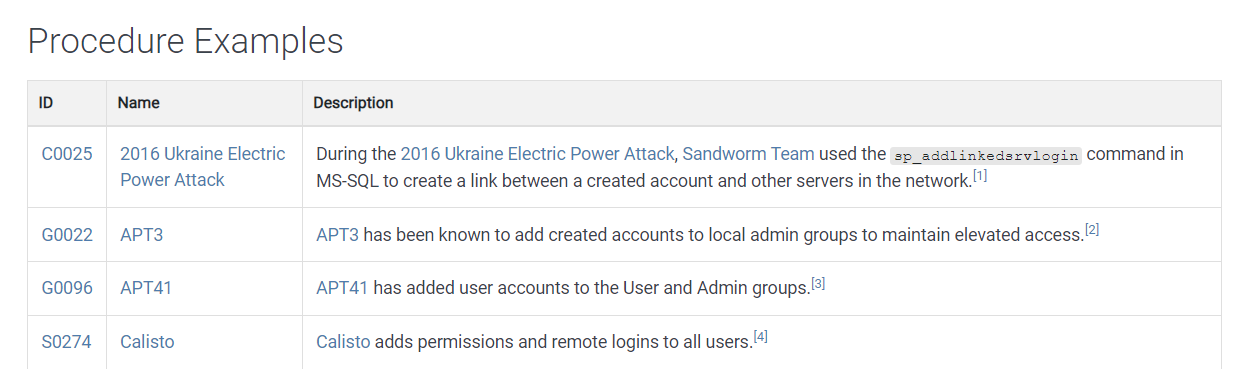
For example, APT 13 creates accounts for local administrator groups to maintain elevated access. (Procedures can fall under multiple techniques and sub-techniques.)
Section 3.4.2: Techniques and Sub-Technique Object Structure
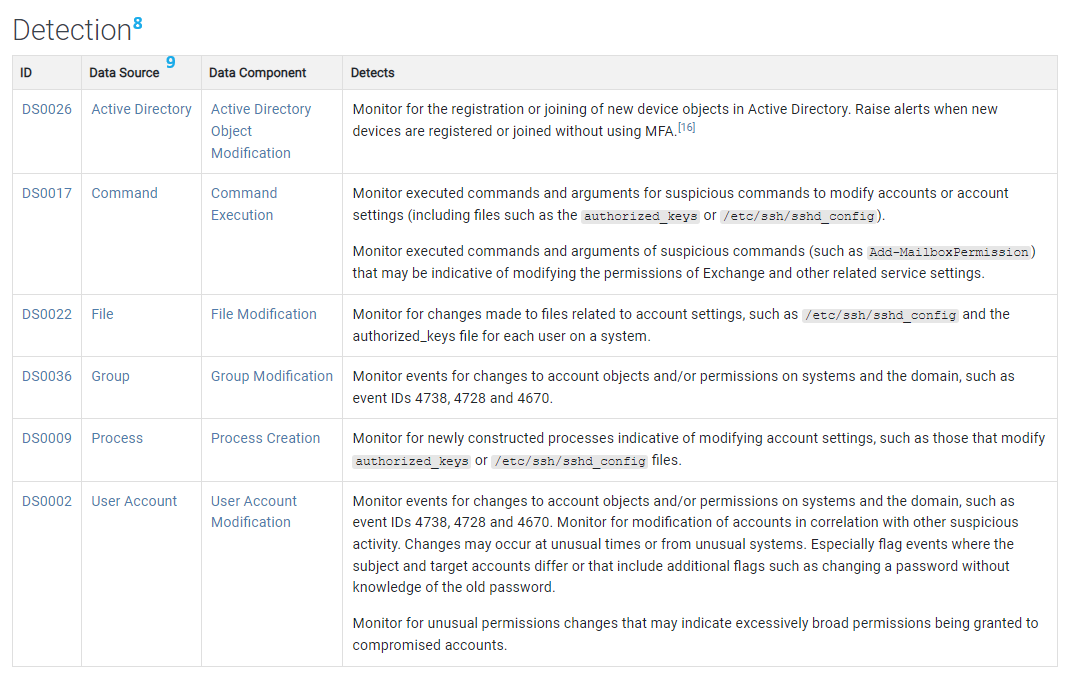
Data Source - where the data is obtained or collected for processing, analysis, or reporting.
The terms below are sections and essential information for each technique and sub-technique.
Always Required:
- Name
- ID
- Sub-Techniques
- Tactic
- Description
- Platform
- Version
- Detection
- Data Source
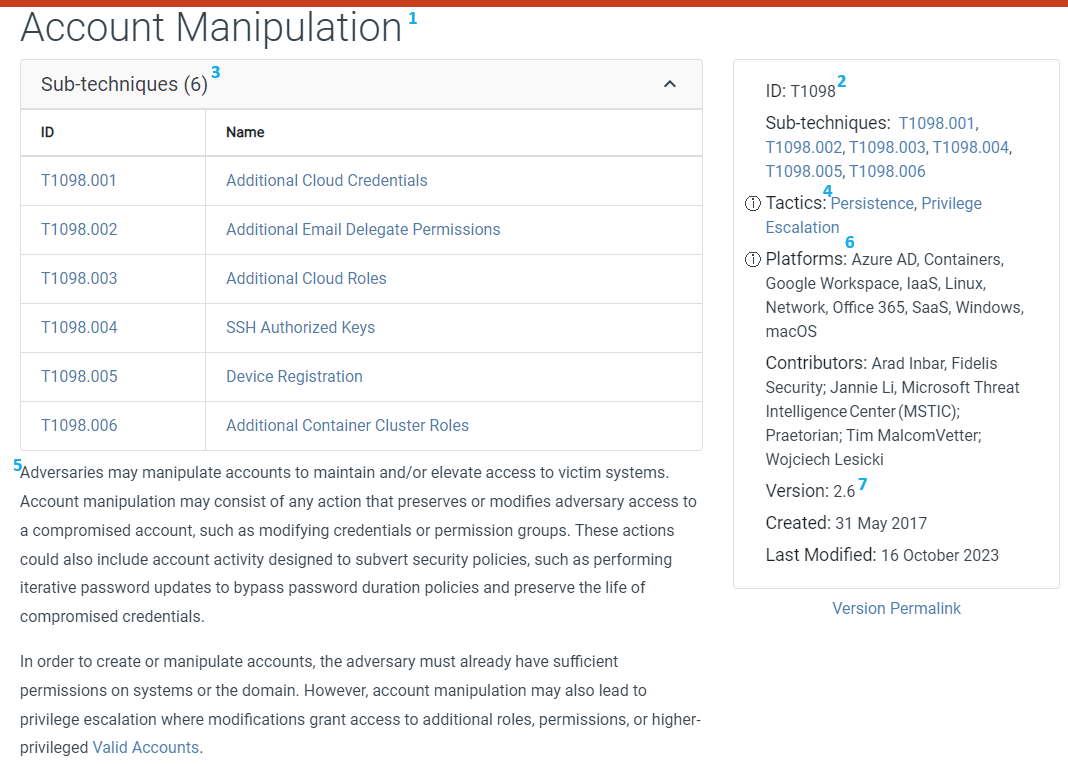
 Account Manipulation
Account ManipulationRequired If Available:
- Mitigation
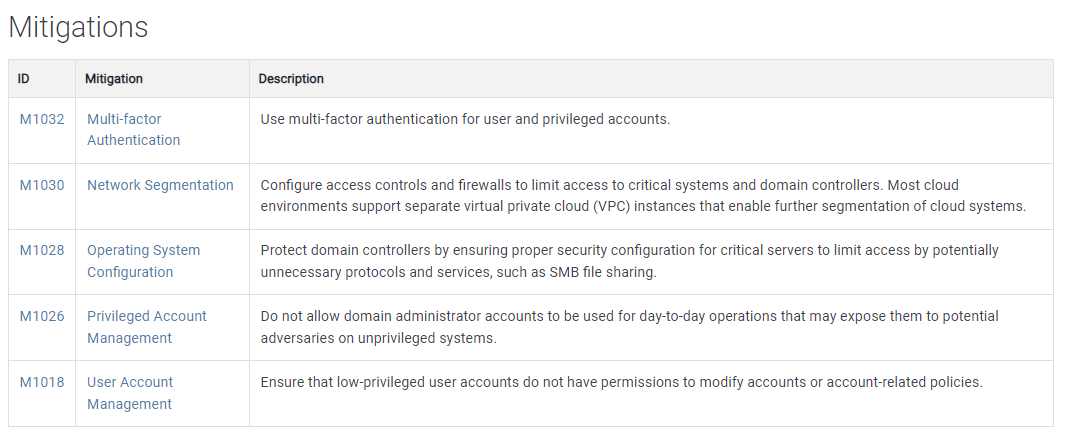 View Larger Image
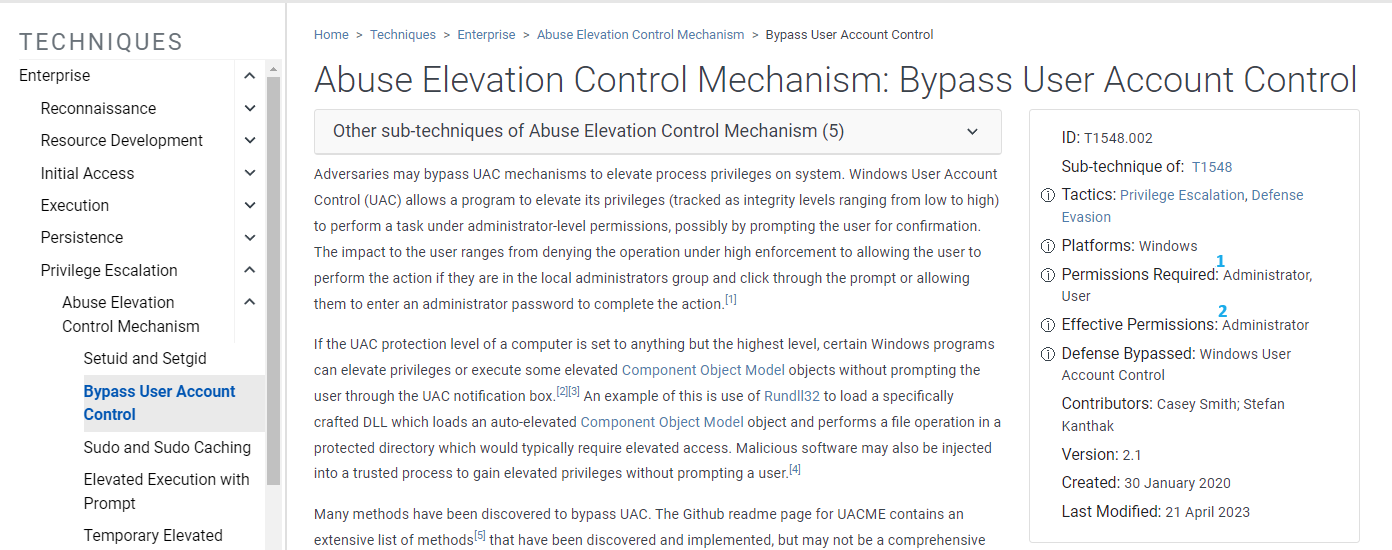
View Larger ImageRequired for Sub-techniques under Privilege Escalation:
- Permissions Required
- Effective Permissions
 View Larger Image
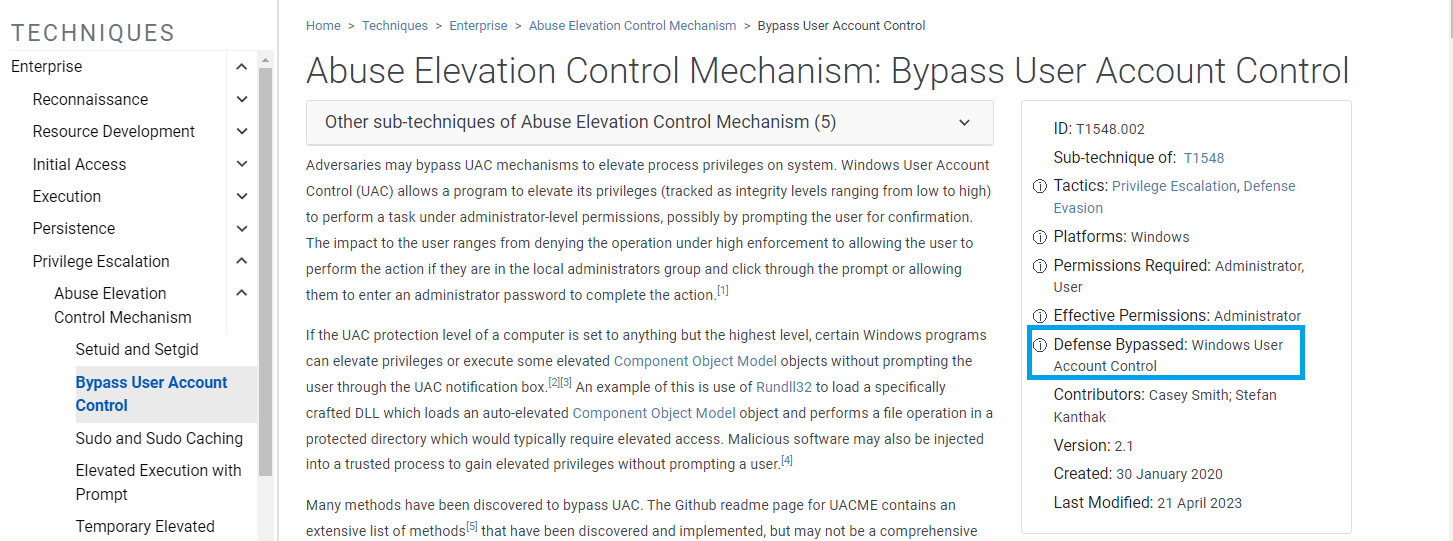
View Larger ImageDefensive Evasion Requirement
"If the (sub-)technique can be used to bypass or evade a particular defensive tool, methodology, or process then the defense bypassed is required to be listed."
 View Larger Image
View Larger ImageOptional
- Link to the Common Attack Pattern Enumeration and Classification ID(CAPEC ID)
- List of non-MITRE individuals and organizations that contributed information from the first to the most recent.
- The procedure example field provides concrete examples of how specific adversary groups or types of software, such as malware and tools that, have been used in real-world scenarios.

List of contributors for Account Manipulation

Procedure Examples for Account Manipulation
Optional Execution Sub-Techniques Information
- System Requirments: Additional information on requirements the adversary needs to meet for an effective attack or about the state of the system, such as software and patch level that may be required for the sub-technique to work, can be listed under system requirements.
- Supports Remote:Whether the sub-technique enables the execution of actions on a system from a remote location.
Section 3.4.3: Sub-Technique Details
Before the addition of sub-techniques in 2020, techniques varied significantly in coverage, with some techniques containing a wide range of behaviors and others scarcely focused on. This inconsistency made the framework challenging to navigate and apply uniformly.
MITRE list the goals they wished to achieve as
- "Make the abstraction level of techniques similar across the knowledge base."
- "Reduce the number of techniques to a manageable level"
- "Provide a structure to allow sub-techniques to be added easily that would decrease theneed to make changes to techniques over time"
- "Demonstrate that techniques are not shallow and can have many ways they can be performed that should be considered"
- "Simplify the process for adding new technology domains to ATT&CK that use overlapping techniques"
- "Enable more detailed data sources and descriptions for how a behavior can be observed on specific platforms"
Considerations
- While a technique may align with multiple tactics, the sub-techniques do not have to apply to all those tactics. For example, a sub-technique under "Process Injection" could also apply to "Defense Evasion" but does not have to apply to any other tactics.
- ATT&CK does not require that every technique have sub-techniques.
- Something you are
- Something you know
- Something you have
- Somewhere you are
- Something you do
- Sub-techniques can be platform-specific, but not all sub-techniques are. For example, network communications may not be because of the platform-agnostic nature of these techniques.
- If specific information associated with sub-techniques is considered relevant to the parent technique the information will up to the parent technique.
Example: Multi-Factor Authentication Interception
When information relevant to sub-techniques also applies to the overarching technique, it will be incorporated into the guidance of the parent technique. For instance, the recommendation to use multi-factor authentication to mitigate against the Additional Cloud Credentials sub-technique is equally effective in preventing Account Manipulation efforts.
Section 3.5: Groups
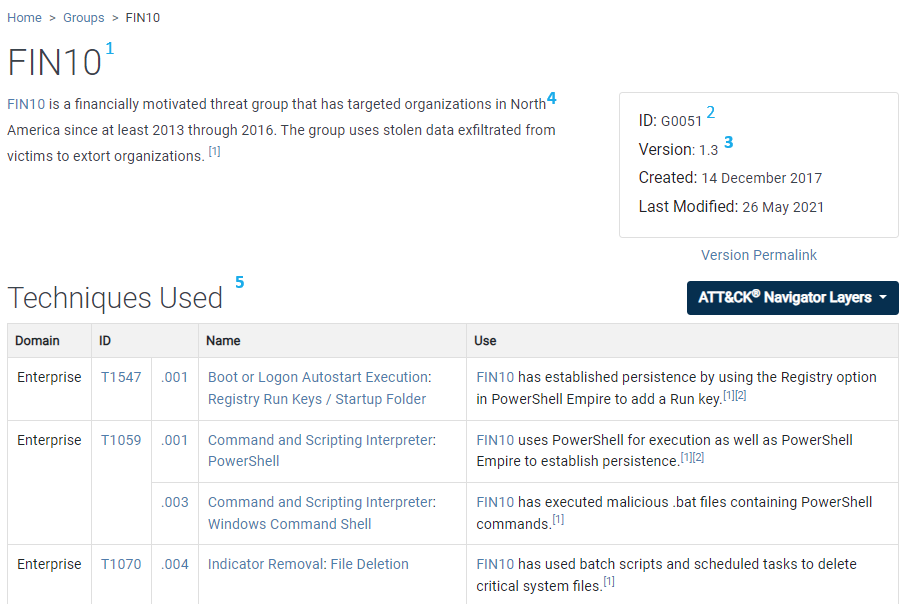
ATT&CK focuses primarily on Advance Persistent Threat (APT) groups, example: APT 19but can also include other advanced groups, example: FIN10.
Section 3.5.1: Groups Object Structure
ATT&CK Group Model
Required
- Name
- ID
- Version
- Description
- Techniques / SubTechniques Used*
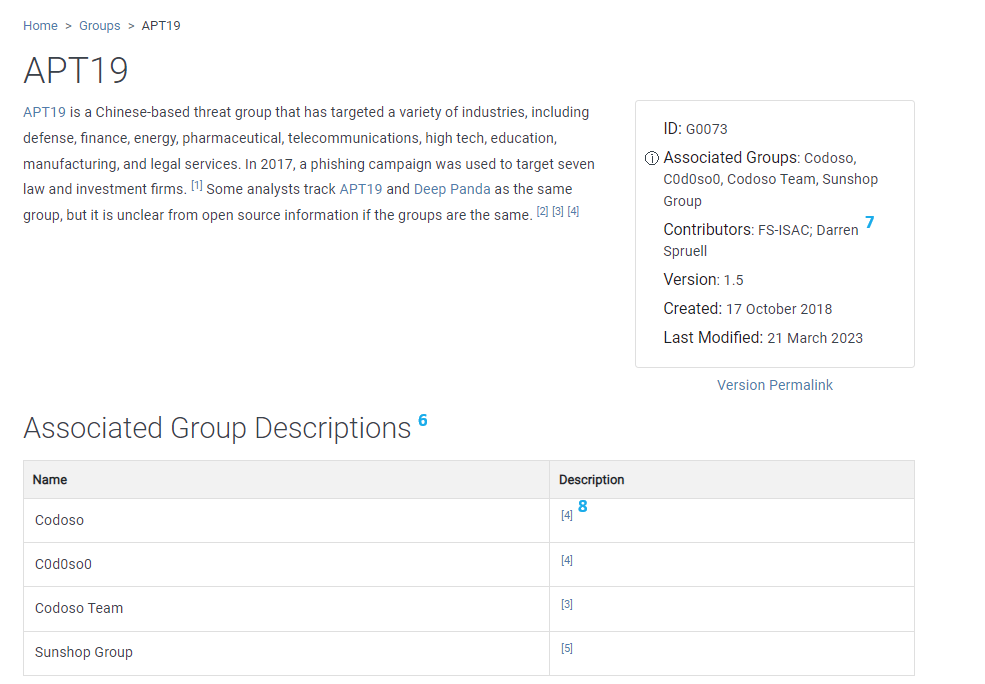
- Associated Groups
- Contributor
- Associated Group Descriptions
- Software
 View Larger Image
View Larger ImageOptional
 View Larger Image
View Larger Image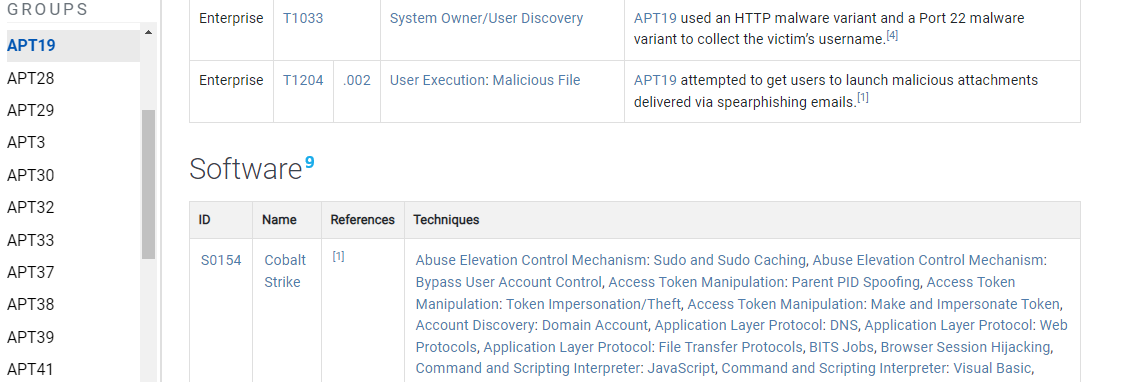 View Larger Image
View Larger ImageComing Soon:
Section 3.6:Software
Section 3.6.1:Software Object Structure
Section 3.7:Mitigations
Section 3.7.1: Mitigation Object Structure
Section 3.8: ATT&CK Object Model Relationships
Section 3.9: Versioning
Section 3.9.1: Objects
Section 3.9.1.1: Techniques and Sub-Techniques
Section 3.9.1.2: Groups
Section 3.9.1.2: Software
Section 3.9.1.2: Matrix
Section 3.9.1.2: Releases
"Additional Information: "The scope of ATT&CK also expands beyond technology domains with PRE-ATT&CK. PREATT&CK covers documentation of adversarial behavior during requirements gathering, reconnaissance, and weaponization before access to a network is obtained." - MITRE